User Management and Security
The User Management and Security module in Wise Municipal Manager provides comprehensive access control, user administration, and permission management capabilities specifically designed for municipal organizations. This module ensures proper segregation of duties, maintains audit trails, and supports compliance with municipal governance requirements.
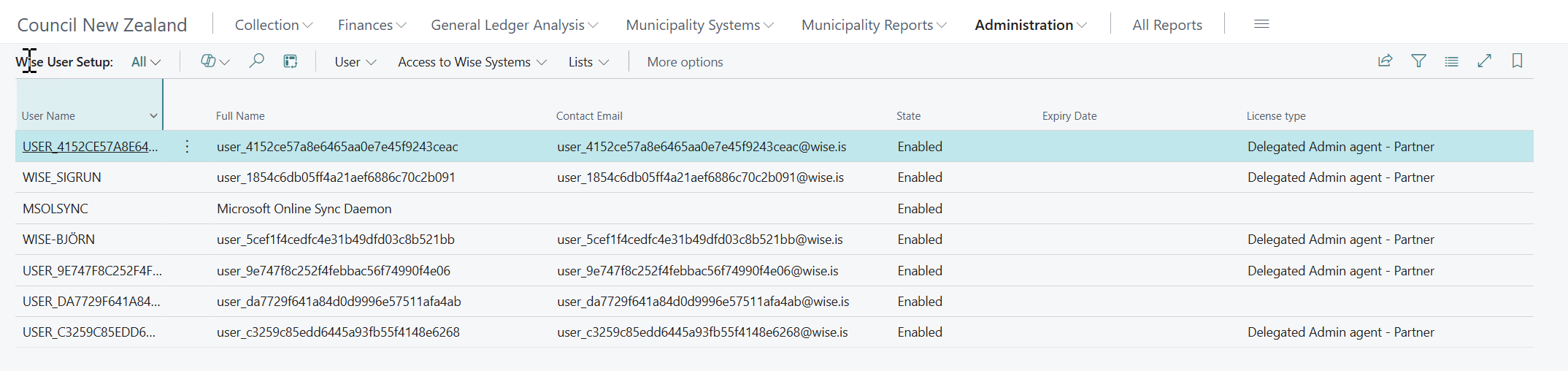
Administration – User setup
Key Features
Advanced User Administration
Centralized User Management: Single interface for managing all municipal system users
Role-Based Access Control: Hierarchical permission structure based on job functions
Profile-Based Setup: Predefined user profiles for common municipal roles
Access Control Lists: Granular permission control for specific system areas
Municipal-Specific Security
Department-Based Access: Control access based on municipal department structure
Service-Area Restrictions: Limit access to specific municipal services
Invoice Processing Security: Specialized permissions for periodic invoicing (RBR)
Resource-Based Filtering: Control access to specific resources and projects
Audit and Compliance
User Activity Tracking: Complete audit trail of user actions
Permission Change Logging: Track all permission modifications
Access Attempt Monitoring: Log successful and failed access attempts
Compliance Reporting: Generate reports for regulatory requirements
User Profile System
Wise User Profiles
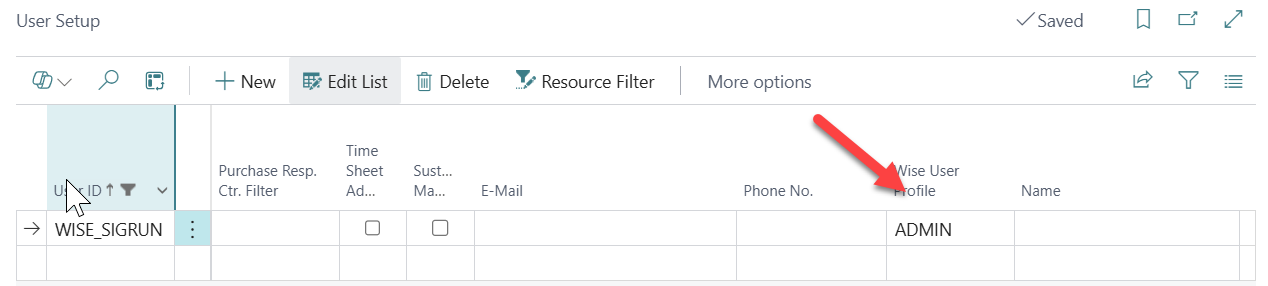
Wise User Profile
Profile Categories
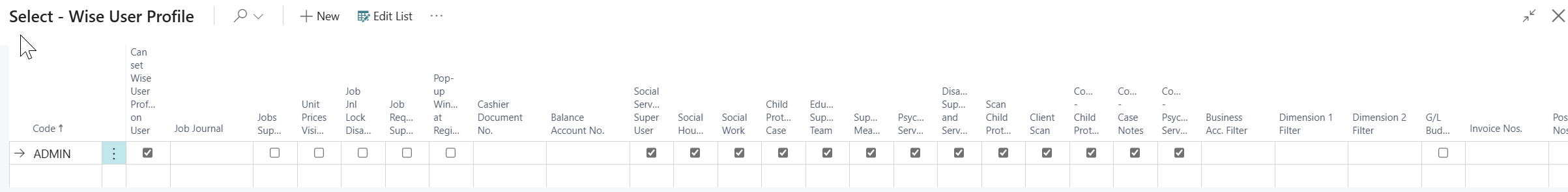
Wise User Profile - Setup
The system supports predefined profiles tailored to municipal organizational structures:
Executive Profiles:
Municipal Manager: Full system access with administrative privileges
Department Head: Department-specific management access
Finance Director: Financial reporting and budget management access
IT Administrator: System configuration and user management privileges
Operational Profiles:
Finance Officer: Accounting, invoicing, and financial transaction access
HR Specialist: Employee and payroll management access
Service Coordinator: Municipal service delivery and customer interaction
Maintenance Supervisor: Work request and asset management access
Support Profiles:
Clerk: Limited data entry and inquiry access
Intern: Read-only access to specified areas
Auditor: Read-only access to all areas for audit purposes
Consultant: Temporary access for specific projects
Profile Configuration
Each profile includes:
Menu Access: Which menu items and pages are visible
Data Permissions: Read, Insert, Modify, Delete rights by table
Functional Access: Access to specific business processes
Reporting Rights: Which reports can be generated and viewed
Export Capabilities: Permission to export data to Excel or other formats
Profile Assignment Process
Screenshot Placeholder: User profile assignment dialog showing user selection and profile options
Assignment Workflow
User Creation: Create user account in Business Central
Profile Selection: Choose appropriate Wise User Profile
Department Assignment: Link user to municipal department(s)
Resource Filtering: Configure resource and project access
Special Permissions: Add role-specific permissions as needed
Bulk Assignment
Department-Wide: Assign profiles to entire departments
Template-Based: Use existing users as templates
Import-Based: Bulk import user assignments from Excel
Organizational Changes: Mass updates during reorganizations
Permission Structure
Standard Business Central Integration
Permission Set Architecture
The system extends Business Central's standard permission model:
Base Permission Sets:
SVE Permissions: Core Wise Municipal Manager permissions
SVE API: API access permissions for external integrations
SVE RBR Periodic Invoicing: Permissions for periodic invoice processing
SVE Salary Permissions: Payroll and salary statement permissions
Permission Inheritance
Role Hierarchies: Junior roles inherit permissions from senior roles
Department Inheritance: Department-specific permission cascading
Function-Based: Permissions grouped by business function
Data Classification: Permissions based on data sensitivity levels
Granular Access Control
Table-Level Permissions
Fine-grained control over data access:
RIMD Permissions:
R (Read): View data without modification capability
I (Insert): Create new records
M (Modify): Edit existing records
D (Delete): Remove records from system
X (Execute): Run pages, reports, and codeunits
Data Classification Levels:
Public: General municipal information
Internal: Department-specific data
Confidential: Sensitive employee or financial data
Restricted: Highly sensitive or regulated information
Field-Level Security
Masked Fields: Hide sensitive information (e.g., social security numbers)
Read-Only Fields: Prevent modification of critical data
Calculated Fields: Display derived information without exposing source data
Time-Based Access: Temporary access to specific fields
Specialized Access Controls
RBR (Periodic Invoicing) Security
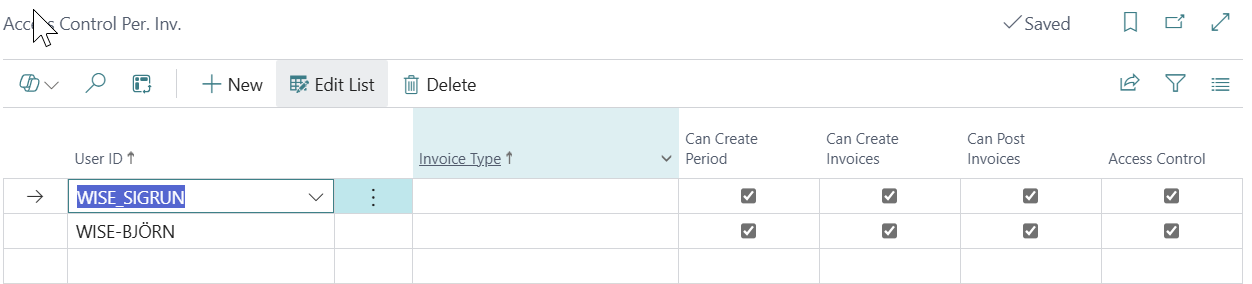
Access Control Per. Inv. (Period Invoices)
RBR Administrator Role
Special permissions for managing periodic invoicing:
Core Privileges:
Can Create Period: Permission to create new invoicing periods
Can Create Invoices: Authority to generate invoices for periods
Can Post Invoices: Permission to post generated invoices
Access Control: Administrative rights over RBR system
Invoice Type Security:
Type-Specific Access: Control by invoice type (utilities, taxes, etc.)
Customer Filtering: Limit access to specific customer groups
Amount Limits: Set maximum amounts for processing
Approval Workflows: Require approval for large transactions
RBR User Assignment
Navigate to User Management → User Administration
Select user for RBR access
Enable RBR Admin User checkbox
System automatically grants required permissions:
Creates access control records
Assigns invoice type permissions
Sets up default restrictions
Resource-Based Security
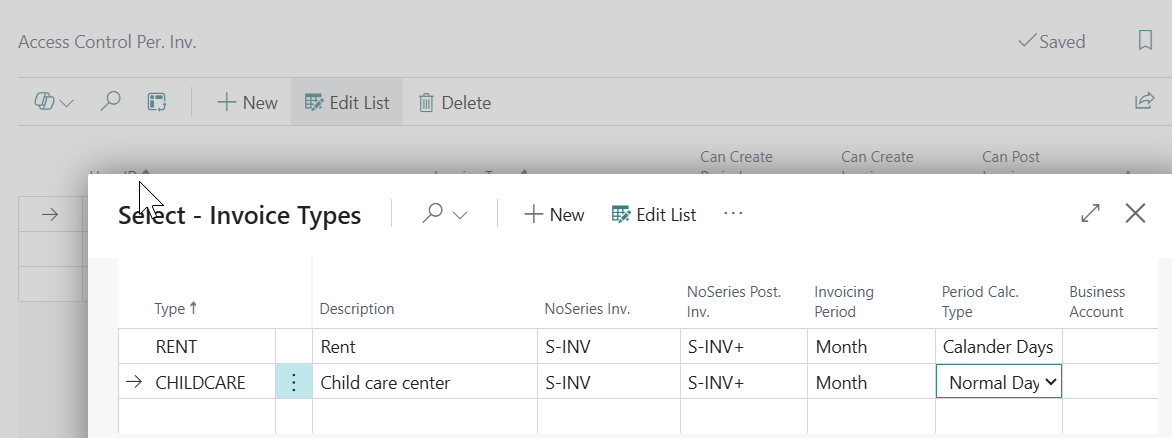
Invoice type - Periodic invoices
Resource Filtering
Control access to specific business resources:
Employee Resource Filters:
Department Limitation: Access only to department employees
Project Assignment: View only assigned project resources
Cost Center: Restrict by cost center assignments
Location-Based: Geographic or facility-based restrictions
Configuration Process:
Access User Setup → Resource Filters
Define filter criteria by user
Set resource types and ranges
Apply time-based restrictions if needed
Limited User Access Control
Screenshot Placeholder: Limited user access control showing field-level restrictions
Advanced Field Restrictions
For users requiring limited system access:
Field-Level Controls:
Visible Fields: Define which fields user can see
Editable Fields: Specify which fields can be modified
Required Fields: Set mandatory field completion
Validation Rules: Custom validation for specific users
Use Cases:
Temporary Staff: Limited access during probationary periods
Contractors: Restricted access to contracted work areas
Interns: Educational access with safety restrictions
External Auditors: Read-only access with audit trail logging
User Administration Interface
Municipality User Administration
Administration Features
Centralized interface for managing all municipal system users:
User Overview:
User List: All system users with current status
Profile Assignment: Current Wise User Profile for each user
Special Roles: RBR Admin and other specialized roles
Last Activity: User login and activity information
Super User Requirements:
Only users with SUPER role can access user administration
Prevents unauthorized permission modifications
Maintains system security integrity
Supports separation of duties
Bulk Operations
Profile Updates: Change profiles for multiple users
Department Reassignment: Move users between departments
Permission Synchronization: Update permissions system-wide
Deactivation: Temporarily or permanently disable user access
Permission Lookup and Troubleshooting
Permission Analysis Tools
Help administrators diagnose access issues:
Permission Lookup:
User Permission Analysis: View all permissions for specific user
Object Access Check: Verify access to specific pages/reports
Missing Permission Detection: Identify missing permissions for desired access
Permission Source Tracking: Determine where permissions originate
Troubleshooting Workflow:
User reports access issue
Administrator runs permission lookup
System identifies missing permissions
Administrator assigns appropriate permission set or profile
User tests access and confirms resolution
Security Best Practices
User Account Management
Screenshot Placeholder: Security checklist showing best practices implementation
Account Lifecycle Management
Onboarding Process: Standardized new user setup
Regular Reviews: Periodic access rights validation
Offboarding: Systematic user deactivation process
Account Monitoring: Active account usage tracking
Password and Authentication
Strong Password Requirements: Municipal-standard password policies
Multi-Factor Authentication: Enhanced security for privileged accounts
Session Management: Automatic logout for inactive sessions
Login Monitoring: Track and alert on suspicious login patterns
Role-Based Security Design
Principle of Least Privilege
Minimum Required Access: Users receive only necessary permissions
Temporary Elevation: Short-term additional access for specific tasks
Regular Validation: Periodic review of user permission requirements
Documentation: Clear documentation of permission rationale
Segregation of Duties
Financial Controls: Separate creation, approval, and posting functions
Asset Management: Separate acquisition, maintenance, and disposal roles
Payroll Processing: Separate data entry, calculation, and payment functions
Audit Independence: Separate audit access from operational functions
Compliance and Auditing
Audit Trail Requirements
User Action Logging: Complete log of user activities
Permission Change Tracking: Record all permission modifications
Data Access Logging: Track access to sensitive information
Report Generation Auditing: Log report generation and distribution
Regulatory Compliance
Municipal Governance: Align with local government requirements
Financial Regulations: Support financial reporting compliance
Privacy Protection: Ensure personal data protection compliance
Audit Standards: Support internal and external audit requirements
Integration with Business Central Security
Native Security Extension
Enhanced Permission Model
Extended Permission Sets: Wise-specific permissions integrated with BC standard
Custom Roles: Municipal-specific roles beyond standard BC roles
Data Classification: Enhanced data sensitivity classification
Field Security: Extended field-level security capabilities
Security Synchronization
User Setup Integration: Wise profiles synchronized with BC user setup
Permission Inheritance: Wise permissions complement BC permissions
Role Center Integration: Security-aware role center customization
Menu Filtering: Dynamic menu filtering based on permissions
External System Integration
API Security
OAuth 2.0 Support: Secure API authentication
Token Management: Secure token generation and validation
Rate Limiting: Protect against API abuse
Audit Logging: Complete API access logging
Single Sign-On (SSO)
Active Directory Integration: Corporate directory synchronization
SAML Support: Identity provider integration
Multi-Domain Support: Support for municipal network structures
Group Membership: Automatic permission assignment based on AD groups
Troubleshooting Common Issues
Access Permission Problems
"You do not have permission to access this page"
Cause: User lacks necessary permission set or profile assignment
Solutions:
Check user's assigned Wise User Profile
Verify Business Central permission set assignments
Confirm user is active and not blocked
Review any resource filters that might restrict access
"Object not found" or Missing Menu Items
Cause: Permission sets not properly assigned or menu customization issues
Solutions:
Assign appropriate SVE Permissions set
Check role center customization
Verify object permissions in permission sets
Clear user personalization if necessary
RBR Access Issues
Cannot Access RBR Invoice Processing
Cause: RBR Administrator rights not properly configured
Solutions:
Navigate to User Administration
Enable RBR Admin User for the user
Verify RBR Access Control records are created
Check invoice type-specific permissions
Cannot Create or Modify Invoice Periods
Cause: Insufficient RBR permissions or access control restrictions
Solutions:
Verify RBR Access Control Per Invoice settings
Check "Can Create Period" permission
Confirm invoice type access rights
Review any customer or amount limitations
Profile and Permission Synchronization
Profile Changes Not Taking Effect
Cause: Permission cache or synchronization delays
Solutions:
Sign out and sign back in to refresh permissions
Check if permission set assignments match profile requirements
Verify profile configuration is complete
Contact system administrator for permission cache refresh
Key Benefits
Enhanced Security: Municipal-specific security model beyond standard ERP
Simplified Administration: Centralized user and permission management
Compliance Support: Built-in support for municipal governance requirements
Audit Trail: Complete tracking of user activities and permission changes
Scalability: Support for large municipal organizations with complex structures
Integration: Seamless integration with Business Central security framework
Flexibility: Configurable to meet specific municipal organizational needs
User Experience: Intuitive interface for both administrators and end users
The User Management and Security module provides municipalities with enterprise-grade security capabilities while maintaining the flexibility needed for diverse municipal operations and organizational structures.
